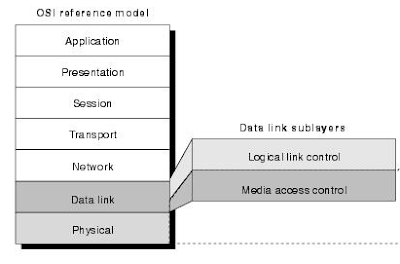
The data link layer is the penultimate or the second lowermost in the OSI model. The data link layer is made up of two sublayers:
- MAC (Media Access Control) Layer
- LLC (Logical Link Control) Layer
Both of these two sublayers are responsible for different functions for the data link layer. Today, we are going to talk about the LLC layer in details.
LLC (Logical Link Control) layer:
LLC layer is also known as the logical link control. As it is evident from the name itself that for the data link layer, the LLC layer serves the purpose of providing end to end flow, error control, and multiplexing different protocols over the Mac layer of the data link layer.
For example:
Let’s assume that I am running Windows 10 and I want to do a video chat with my friend who is sitting across oceans in Germany. Now, here is what happens when we start the video chat:
Multiplexing
So when I start video chatting, my application, that maybe Skype, starts generating video data packets. However, the data link layer has some restrictions like a packet size cannot be greater than a particular size, let’s say X bytes in total. That implies that the data packets have to be broken down into different chunks and those data packets have to be transmitted chunk by chunk.
Why so?
Let’s say you send data packets of longer sizes. Then, if that data packet is lost, you will have to send those packets once again. And the larger the size of the packet is, the larger bandwidth will be required to resend those data packets. That’s why an optimized frame size has been defined for the size of a data packet for data link layer.
So, now the data packets have been broken into frames and they will be sent chunk by chunk across the internet. So when my data link layer breaks the videos in chunks, it is smart enough to mark those frames with some cues. This allows my friend’s data link layer to exactly know the order of the frames so that it can re-arrange the frames back in order.
Flow control
Another thing that LLC layer is responsible for is flow control. Let’s take a look at the flow control this way.
I am a not-so-rich person so I cannot afford a laptop and I am still working on old Windows PC with 256 Mb RAM. On the other hand, my girlfriend can afford a brand new laptop that was just launched in the market.
So when we video chat, because of the HD quality camera from her laptop, the video size I receive outsizes my video sent to her from my poor camera. Does that mean that we should run out of sync? No, that does not happen, right?
And that’s where exactly flow control comes into the picture. LLC layer makes sure that one fast computer does not overrun a slower one. For that purpose, the concept of ‘Ack’ acknowledgment has come into the picture. For every frame received or sent, I must send/receive an ack respectively to be in sync.
Error control
LLC layer uses CRC (Cyclic Redundancy Check) to check frame errors at data link layer. This is more like providing a preview of a bigger picture to your friend that where he/ she is going wrong.
MAC (Media Access Layer) layer:
MAC layer is also known as Media Access Layer. As it is evident from the name itself that for the Data link layer, the MAC layer serves the purpose of managing the media access to different devices.
For example:
Let’s say there is a bus topology in which many computers are connected in a series. However, there is only one common media cable on which all the data has to be transferred.
We know the data is carried over on a cable in terms of electric signals. So, if more than one computer sends an electric signal at the same time, there will be a signal collision which will turn into the data packets loss on the wire. And that’s where MAC layer comes into the picture.
Channel access control Mechanisms applied by Mac layer:
Different kind of channel access control mechanisms are applied by the MAC layer for media access and here are some of the popular channel access control mechanisms:
- Token passing
- CSMA/ CD
- CSMA/ CA
- Slotting mechanism etc.
Token Passing:
A token is passed among the data competitors for a limited amount of time to release the data on the common channel. There are many variants of this mechanisms. Here are some:
- For the quality of service, the token is passed for longer times to a particular node
- A node with more data gets the token for the longer time.
CSMA/ CD:
CSMA/ CD stand for Carrier sense multiple access with collision detection (CSMA/CD). It’s a media access control method used most notably in local area networking using early Ethernet technology.
When two nodes send data packet at the same time, then a collision happens. When a collision happens, a jam signal is sent along the wire which tells all the nodes that there has been a collision in the wire. All the nodes stop sending data for a while, for a random time interval before resuming the sending process again.
CSMA/ CA:
CSMA/ CA stand for Carrier sense multiple access with collision Avoidance (CSMA/CA).
CSMA/ CA came into the picture because the problem with CSMA/ CD was that it detected collision after it happened. That means the damage was already done and the mechanism was looking for the recovery after the damage.
However, in the case of CSMA/ CA, the data packet will only be sent if the media is free from packets. When a node senses that there is some transmission going on the media channel then it will wait for a random time before sensing the media channel once again.
Slots:
Slotting mechanism mostly came from the Aloha system. However, the Aloha system has also seen a lot of modifications.
Like in pure aloha, all the nodes sent packets at any time but this mechanism was improved in slotted aloha where all the nodes could send packets only at the beginning, at one slot.